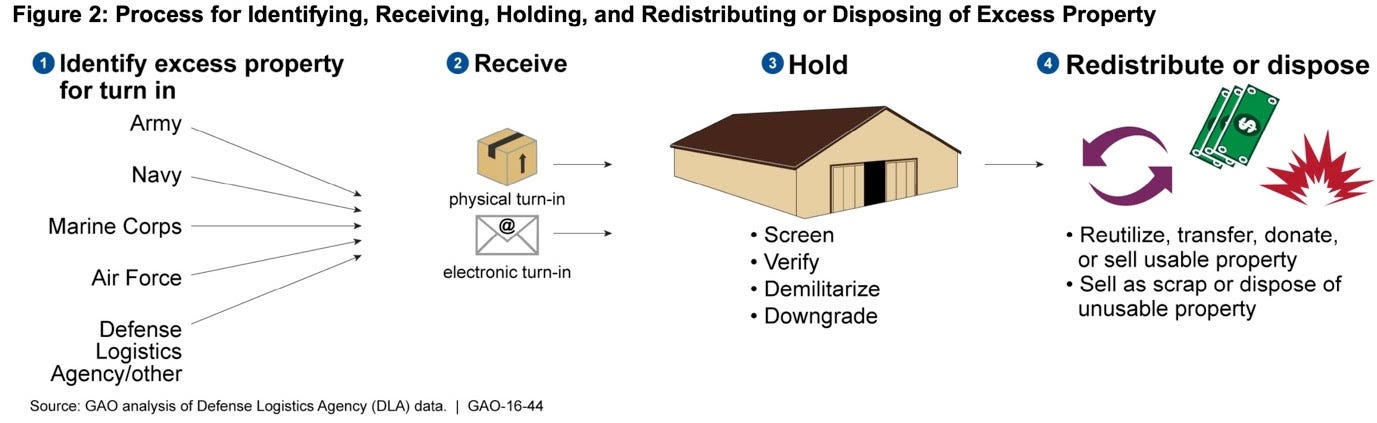
Securing, protecting, and managing data - Storage Best Practices for Data and Analytics Applications
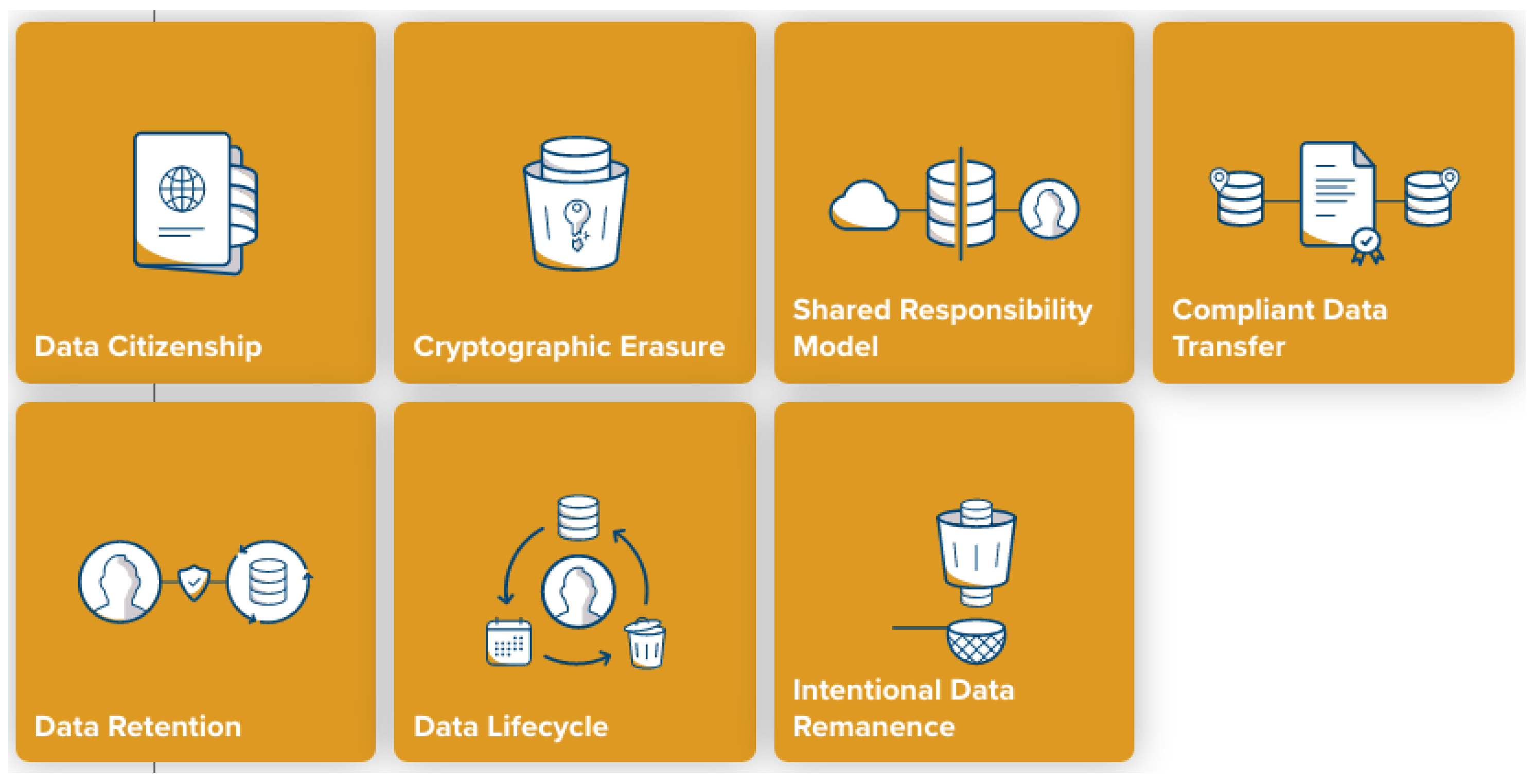
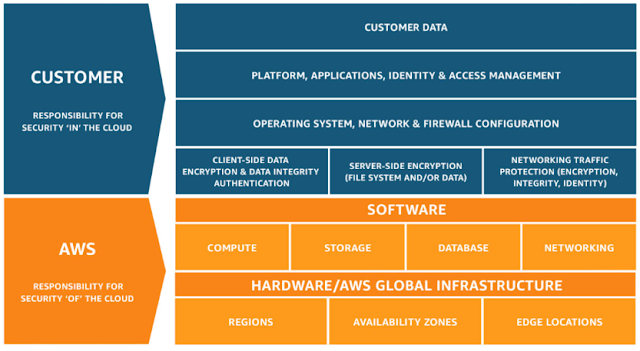
Computers | Free Full-Text | Security Pattern for Cloud SaaS: From System and Data Security to Privacy Case Study in AWS and Azure | HTML
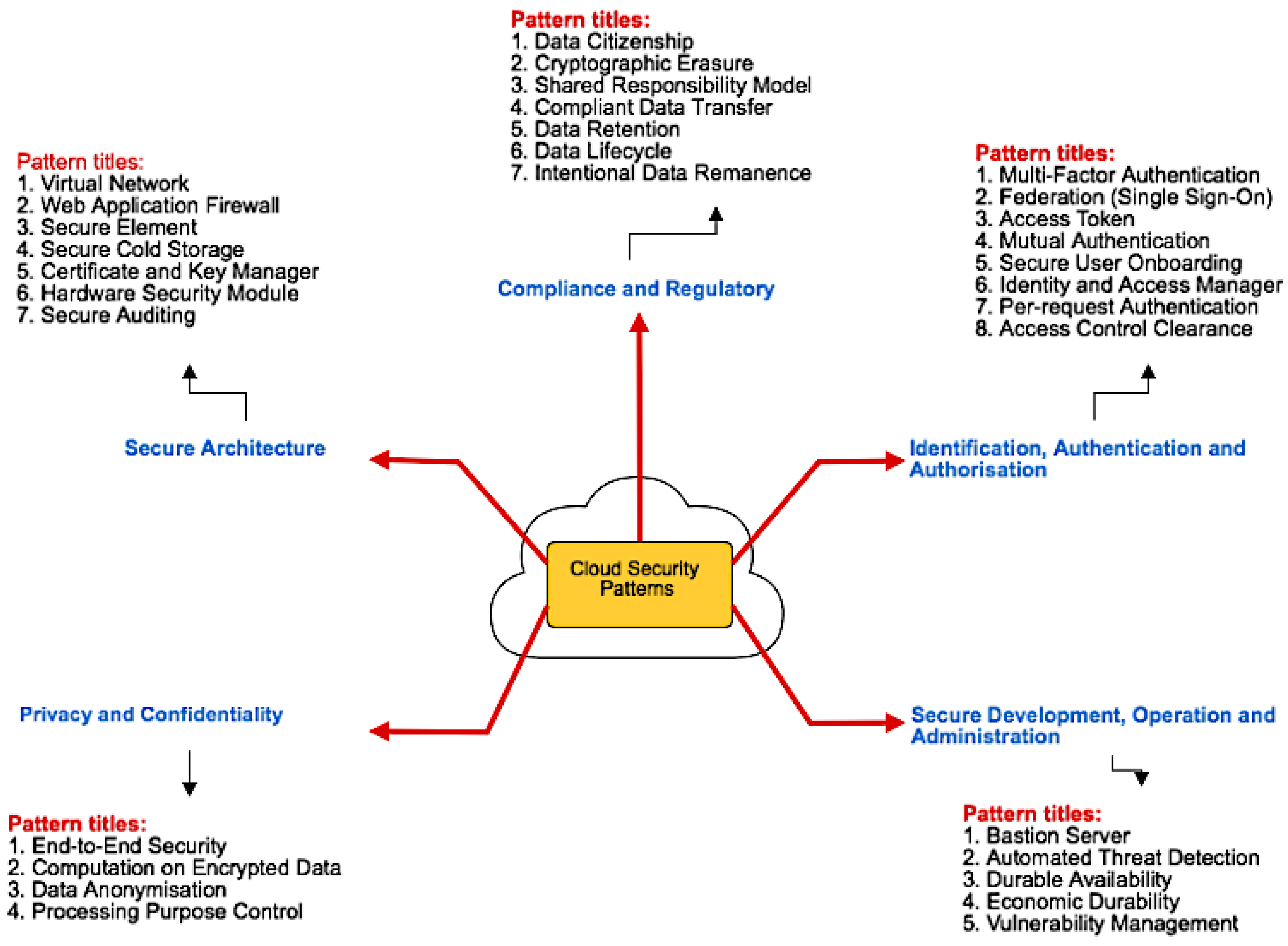
Computers | Free Full-Text | Security Pattern for Cloud SaaS: From System and Data Security to Privacy Case Study in AWS and Azure | HTML
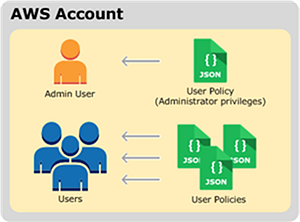
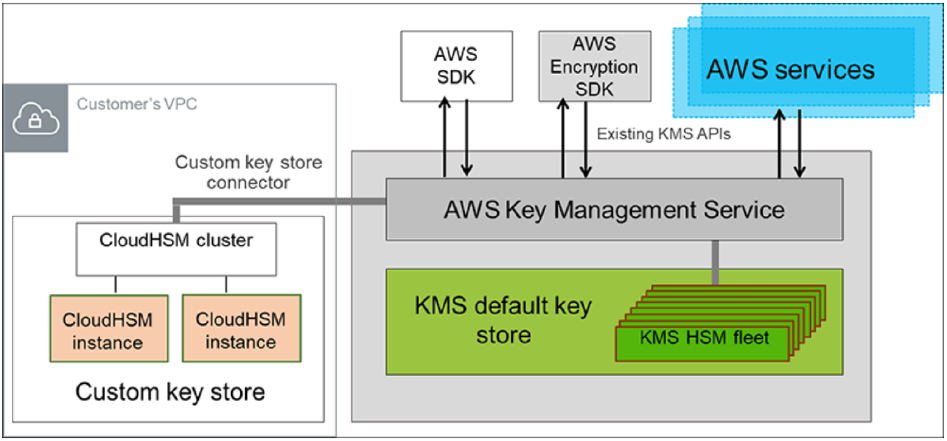
Securing, protecting, and managing data - Storage Best Practices for Data and Analytics Applications