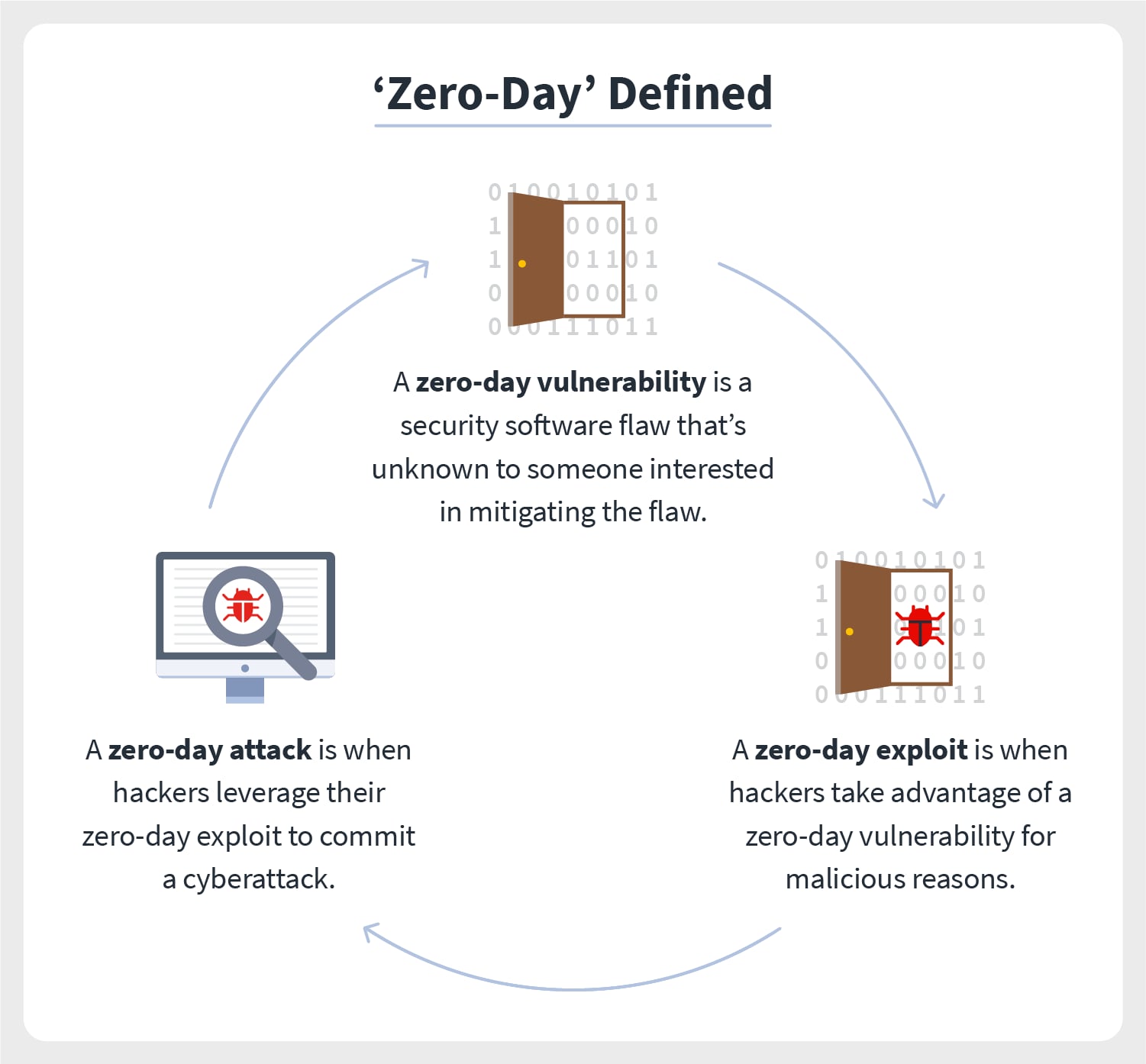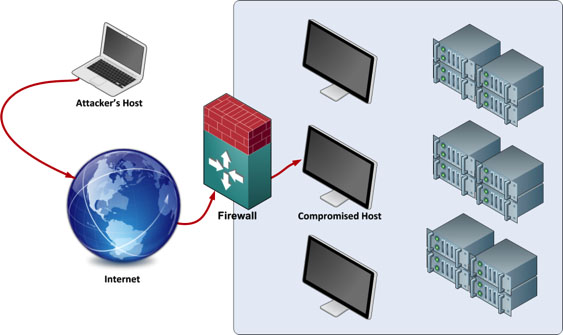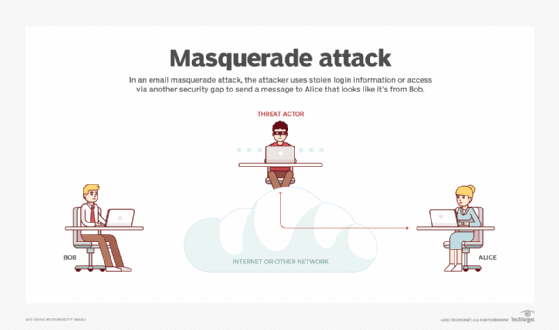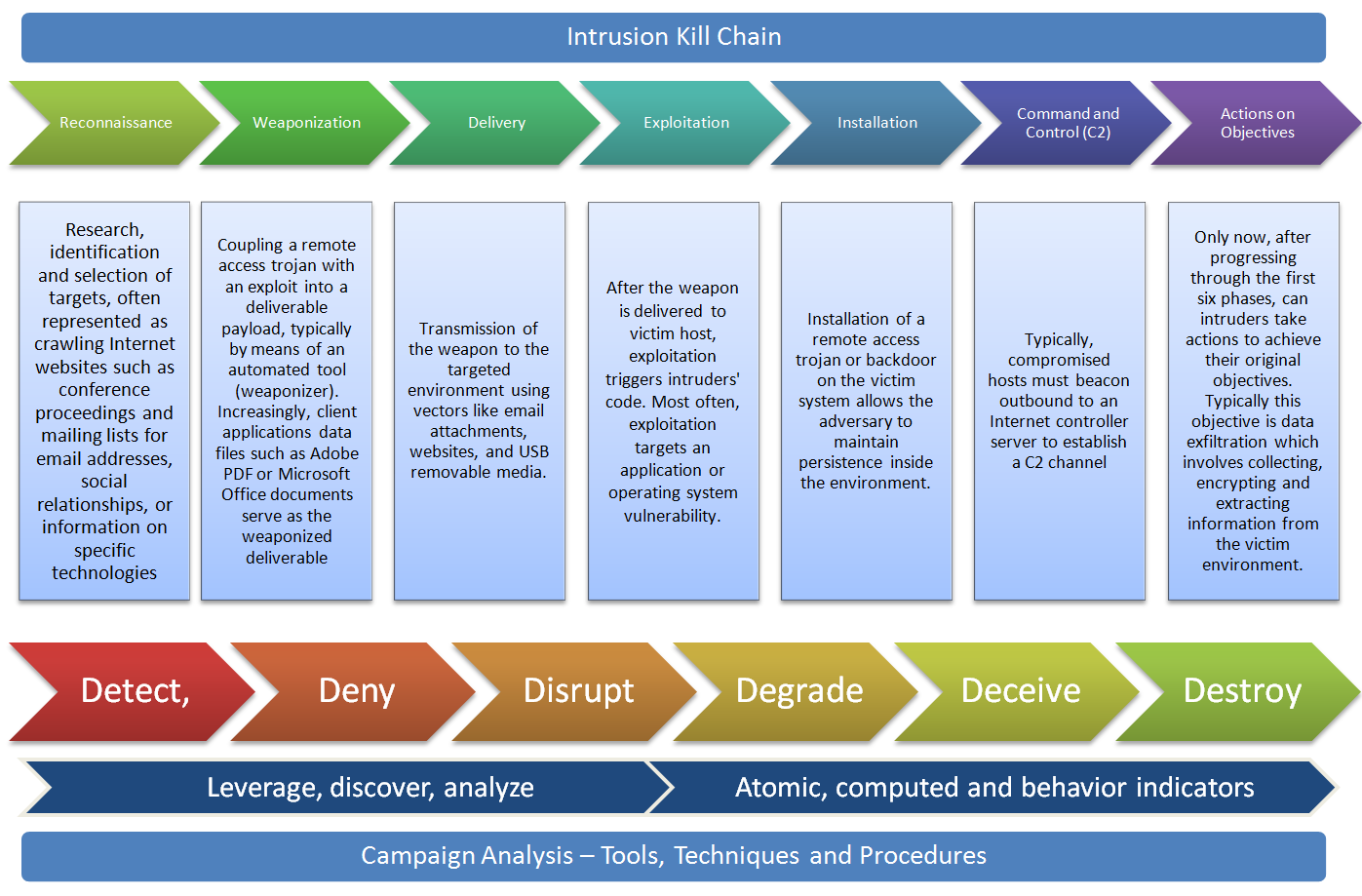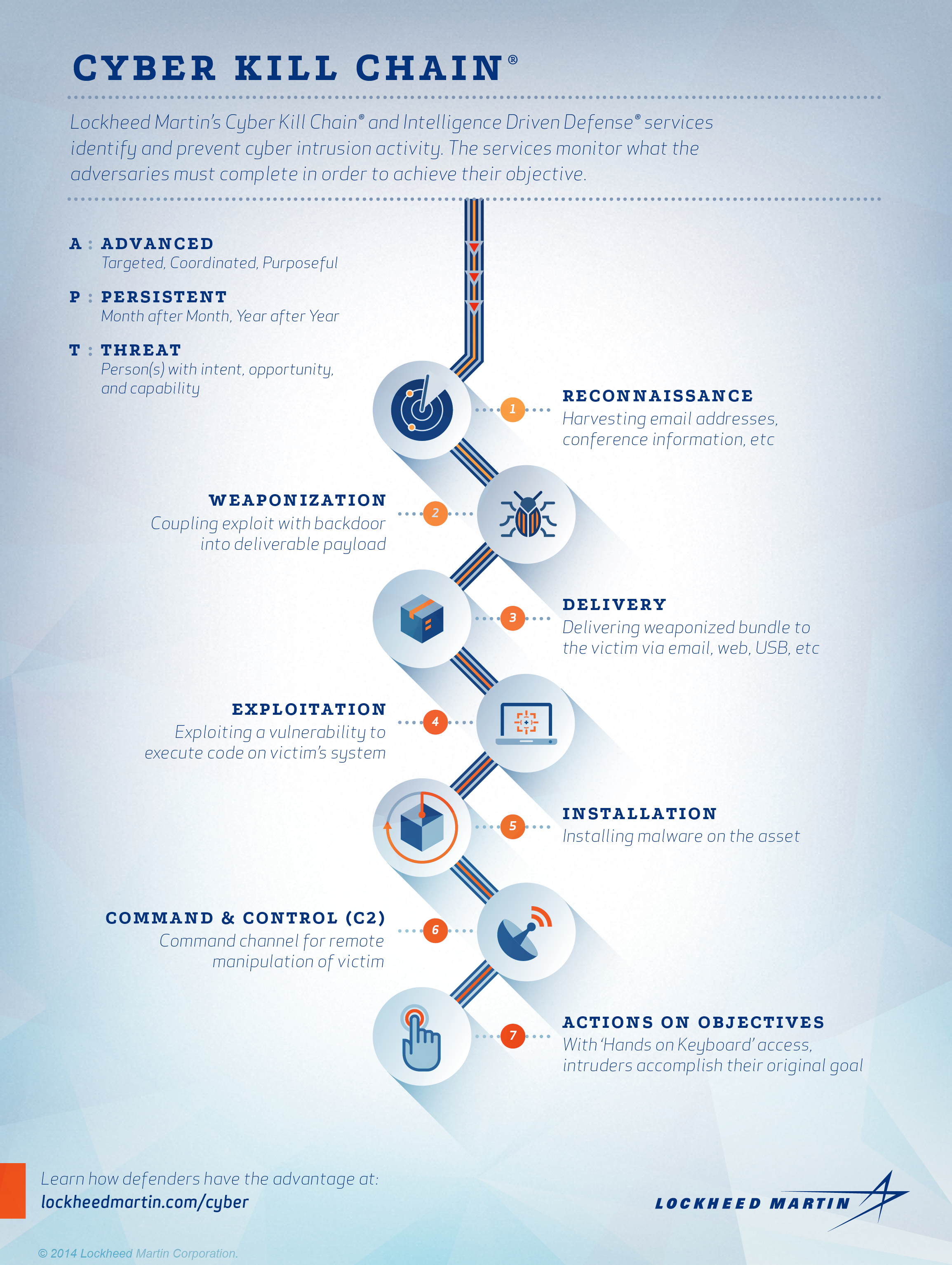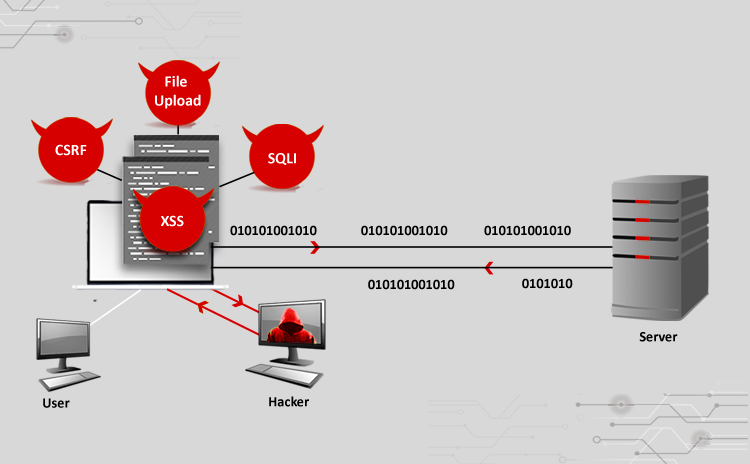
Cyber Attacks Explained - Web Exploitation - Cyber Security Blogs - Valency Networks - Best VAPT Penetration Testing Cyber Security Company - Pune Mumbai Hyderabad Delhi Bangalore Ahmedabad Kolkata India Dubai Bahrain

RVAsec 2018: Robert Mitchell - A Game Theoretic Model of Computer Network Exploitation Campaigns - YouTube