Post-Quantum Cryptography: What Advancements in Quantum Computing Mean for IT Professionals | Semantic Scholar
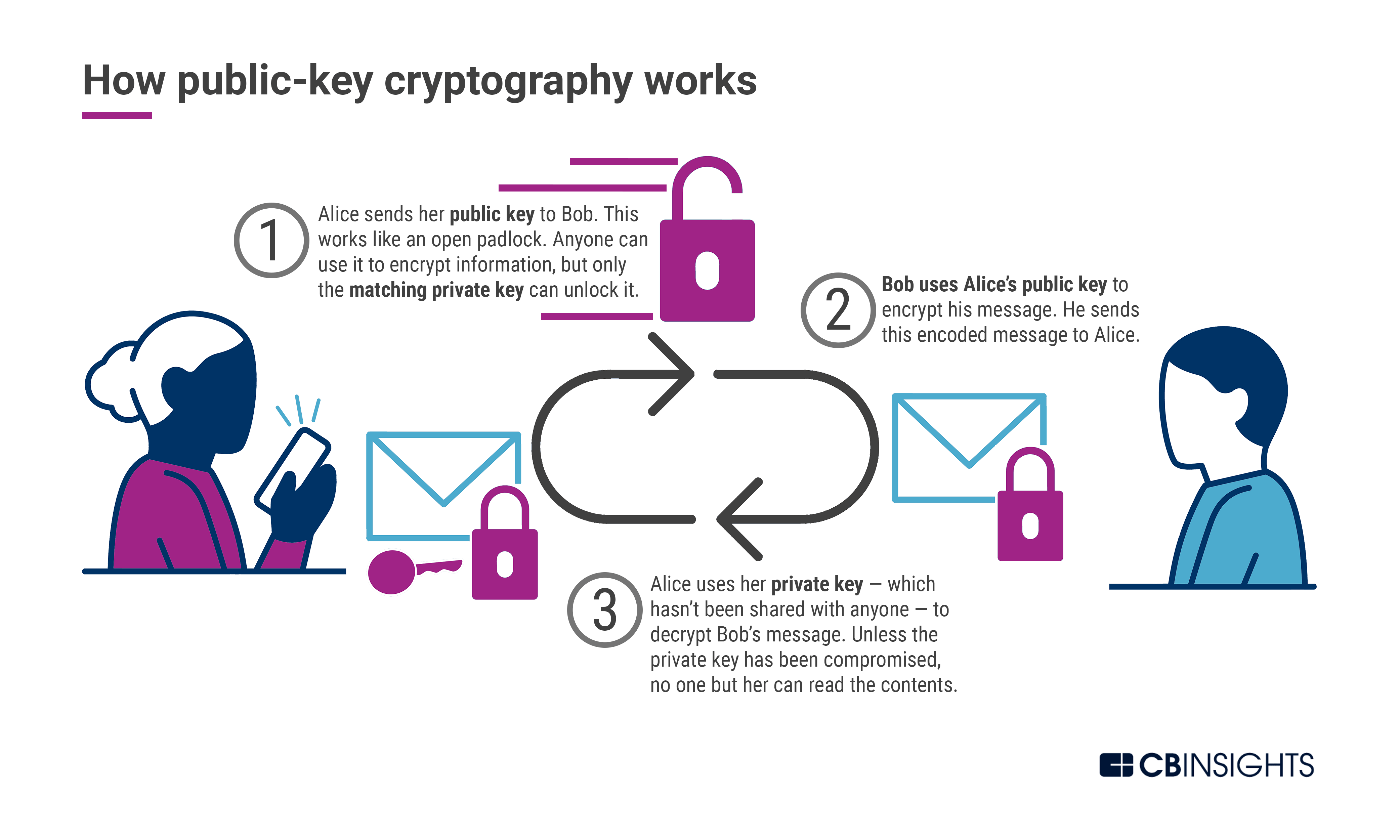
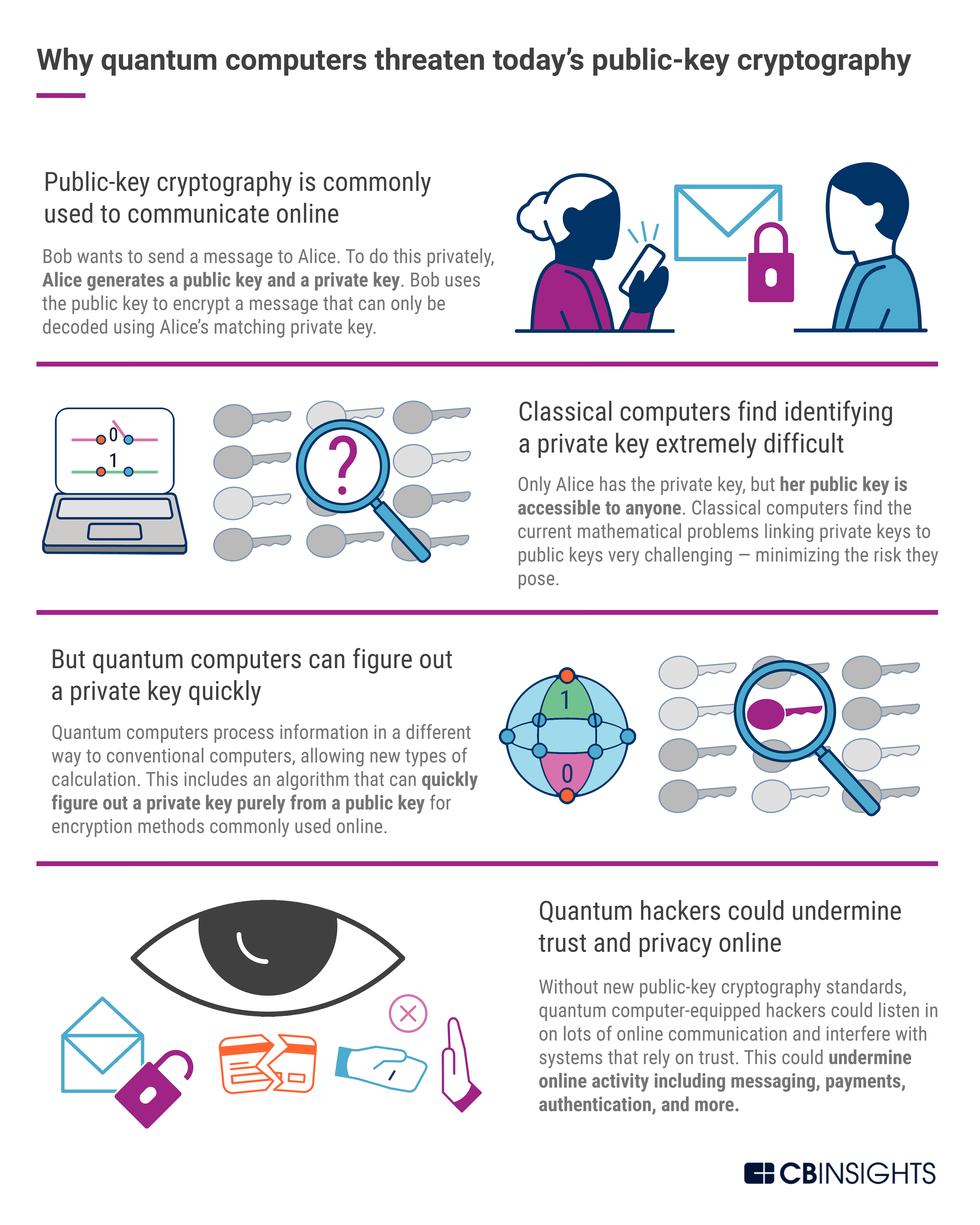
Post-Quantum Cryptography: A Look At How To Withstand Quantum Computer Cyber Attacks - CB Insights Research

NCI Agency | NATO Cyber Security Centre experiments with secure network capable of withstanding attack by quantum computers

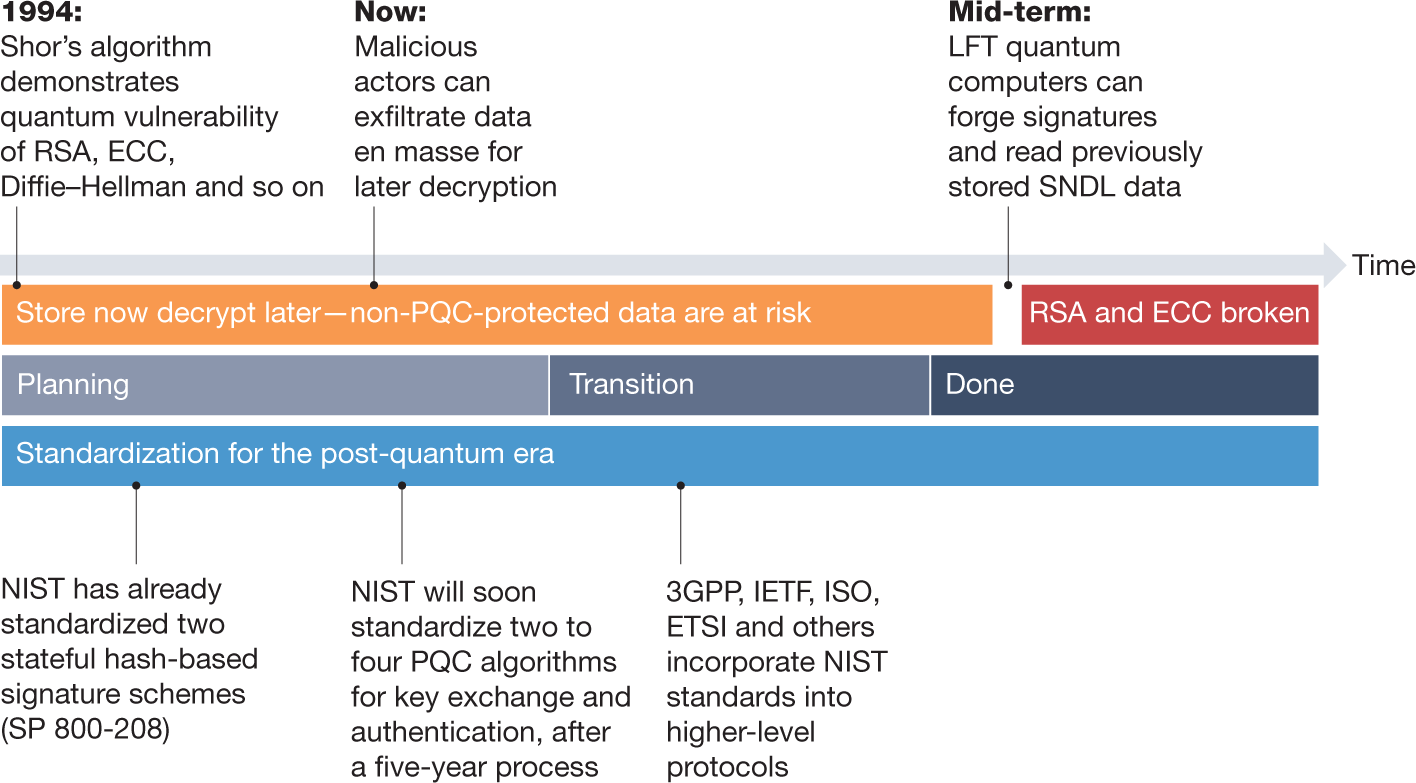
Ready for tomorrow: Infineon demonstrates first post-quantum cryptography on a contactless security chip - Infineon Technologies