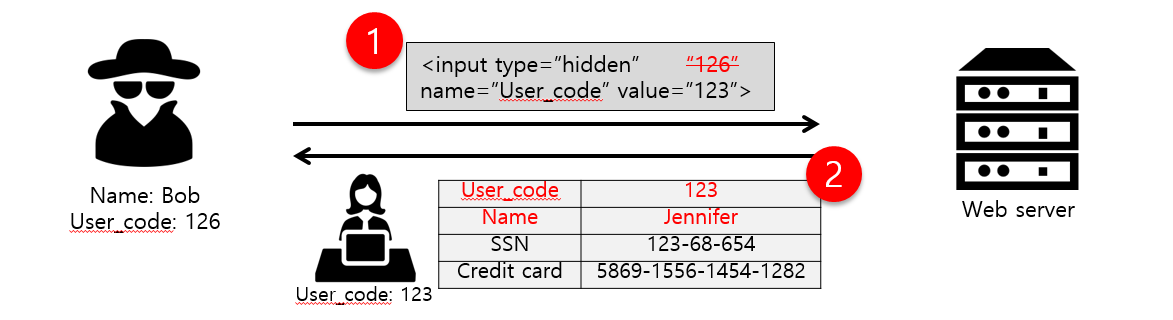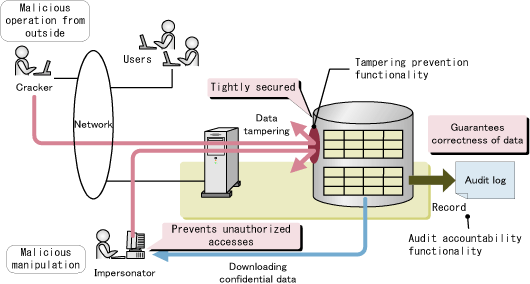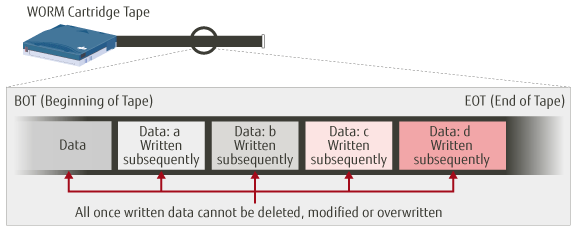
WORM (Write Once Read Many) Function Data tampering prevention and original content retention : Fujitsu Global

Database Tampering and Detection of Data Fraud by Using the Forensic Scrutiny Technique | Semantic Scholar

GitHub - awslabs/tamper-proof-quality-data-using-amazon-qldb: This solution prevents attackers from tampering with quality data by using Amazon Quantum Ledger Database (Amazon QLDB) to maintain an accurate history of data changes.

PCI Requirement 9.9 – Protect Devices That Capture Payment Card Data via Direct Physical Interaction
![Binaryworld - Create and verify digital signature to detect data tampering. ... [ VB -> Cryptography ] Binaryworld - Create and verify digital signature to detect data tampering. ... [ VB -> Cryptography ]](https://binaryworld.net/Main/Articles/Lang1/Cat18/Code3830/screen3830.jpg)
Binaryworld - Create and verify digital signature to detect data tampering. ... [ VB -> Cryptography ]